
The MITRE ATT&CK framework is evolving and it is becoming common to observe that BlueTeam teams have made it one of their detection repositories. For good reason, the latter brings together more than 250 attack techniques and it is a whole community of experts who strive to regularly update this knowledge base.
Through this post, we will present what the MITRE ATT&CK framework is, in what context to use it and finally to what extent it can facilitate the work of BlueTeam teams.
Presentation of the MITRE ATT&CK framework
MITRE is a non-profit organization, renowned in the field of cybersecurity and whose vocation is to “solve problems to make the world safer”.
With the ATT&CK framework, the MITRE organization provides the community with an important empirical knowledge base of the various known attack techniques. Unlike other projects in the field, the focus is not on tools or malware but on the actions taken by an attacker against any system.
This knowledge base has many advantages, it is:
- Freely accessible on the Internet via the MITRE website
- Focused on the actions performed by an attacker on a system, not on exploit tools and malware
- Relatively complete with over 250 Listed Attack Techniques (TTP)
- Representative of attacks observed in the real world
- Updated regularly with several updates per year
Another advantage and not the least, all techniques are fully documented.
For example, the screenshots below describe the Kerberoasting attack technique referenced in the MITRE ATT&CK knowledge base.
First of all, there is a simplified description of the attack technique with many links to additional resources to learn more about the technique in question:
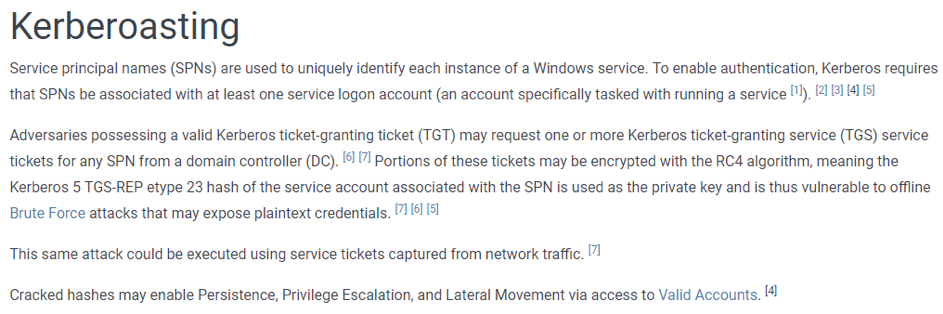
Then we find some examples of offensive tools to perform this attack technique:
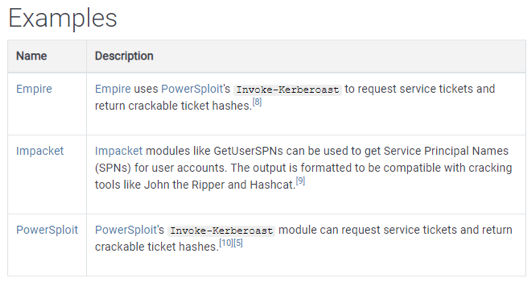
Finally, there are detection indices and remediation actions to prevent this type of technique:
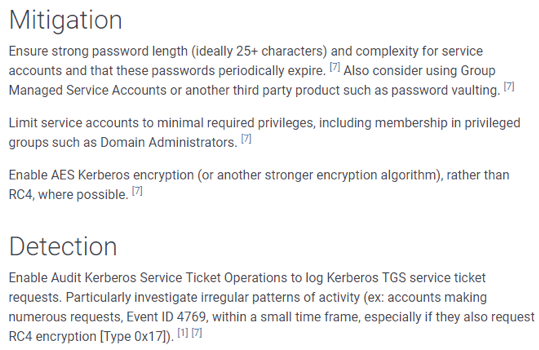
All techniques are logically classified into several categories called tactical.
A tactic represents one of the main objectives targeted by an attacker during an action on an information system. Since the last update of April 2019, there are 12 where we find for example:
- Discovery: The attacker seeks to collect information about the information system in order to prepare his attack. Examples of related techniques: host and port scanning, network share search, sniffing.
- Execution: The attacker attempts to execute a program or other component that could be beneficial to him to carry out his attack. Examples of related techniques: Running a PowerShell script, scheduled tasks, loading DLLs.
- Exfiltration: The attacker attempts to exfiltrate data to a destination under his control. Examples of related techniques: exfiltration through an alternative network protocol to a remote machine under its control, exfiltration from a physical device (USB key, smartphone, MP3 player, …).
- Etc.
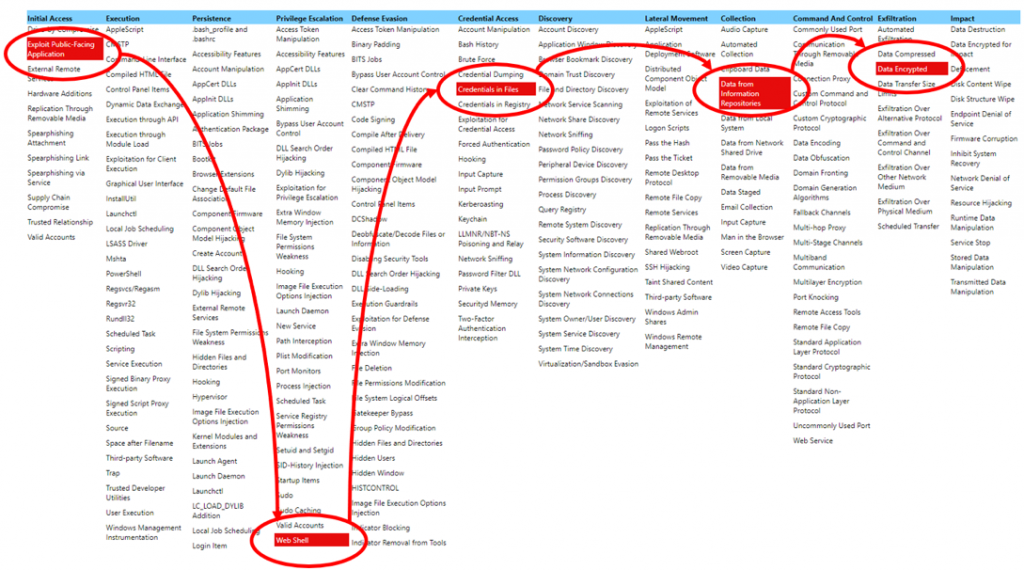
The MITRE ATT&CK matrix, is therefore a representation that makes the correspondence between tactics (columns) and techniques:
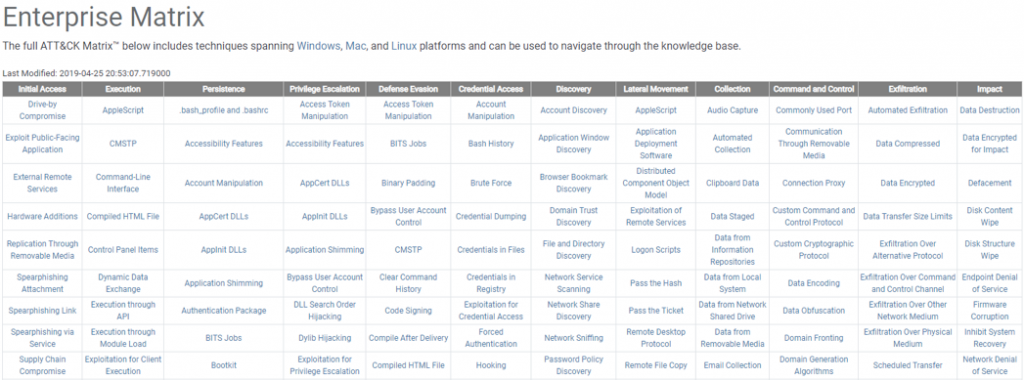
The MITRE ATT&CK matrix responds to a simple need to create an up-to-date baseline of attack techniques grouped by objective (tactics). With a more complete view of offensive techniques, BlueTeam teams can more effectively detect and qualify abnormal events.
MITRE ATT&CK: what are the uses for BlueTeam and security incident detection?
As a reminder, a Blue Team is defined as follows:
A group that defends a company’s information system when an offensive group (i.e., the Red Team) carries out an operational exercise based on rules established and supervised by a neutral group (i.e., the White Team).
The MITRE ATT&CK matrix can therefore help the Blue Team in 3 aspects:
The Threat Intelligence: ATT&CK allows security analysts to standardize how they share knowledge about potential threats:
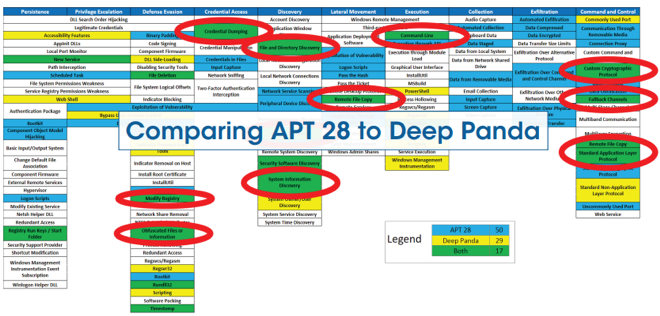
The attack simulation: This greatly facilitates exchanges between the BlueTeam and RedTeam teams by defining a common structure during an attack simulation. Many tools are offered in the ATT&CK framework to test different attack scenarios such as Python CALDERA scripts for example.
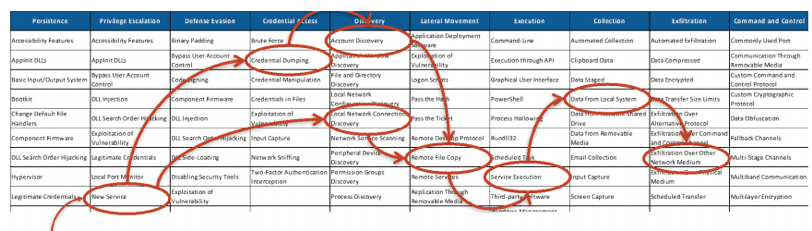
An assessment of the level of defence: The matrix allows BlueTeam teams to have an accurate representation of the different attack techniques covered by security equipment.
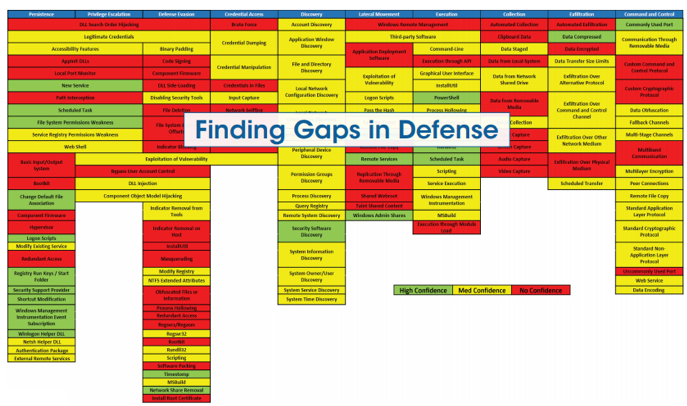
This last use is particularly interesting to control the coverage rate of detection mechanisms. For example, it is utopian to hope to cover all attack techniques by relying exclusively on the events of a firewall or an Active Directory.
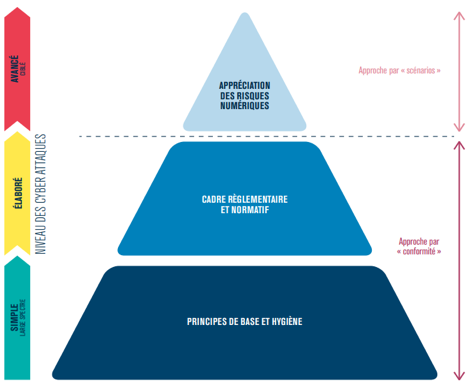
It is therefore a “scenario” approach, as recommended by ANSSI in the EBIOS Risk Manager repository, which is preferred to take full advantage of this framework. (our detailed article on EBIOS Risk Manager).
An example of using the MITRE ATT&CK framework:
Let’s take the simple example of an attempt to exfiltrate the client base of a web application.
A possible attack scenario would be:
- Attacker exploits an application vulnerability to upload a webshell (script that allows the web server to execute commands)
- The attacker downloads the local database configuration file containing the login/password pair used by the web application to connect to the database
- The attacker reuses this account to connect to the database and then makes a copy of the user database in a text file
- The attacker exfiltrates the text file that he has previously encrypted to a remote server under his control
This scenario is composed of several attack techniques referenced in the ATT&CK matrix.
Conclusion
The MITRE ATT&CK framework is now an important ally for BlueTeam teams, providing them with a comprehensive and well-documented repository of attack techniques. Constantly evolving and supported by a growing community, it is gradually adopted and highlighted by security solution publishers as a guarantee of seriousness and quality in the field of cybersecurity. Finally, we can only encourage cybersecurity professionals to discover or even adopt this framework because it is by understanding offensive techniques that it becomes possible to defend themselves effectively.


